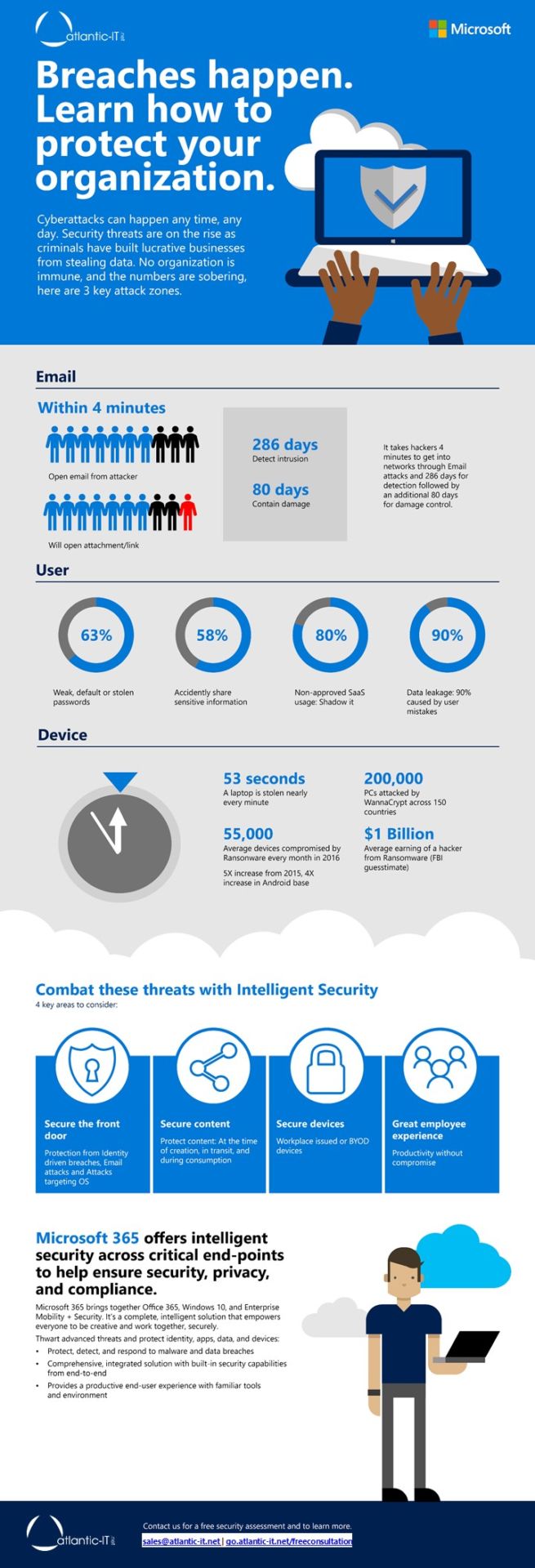
Protect yourself from a Cybersecurity breach with Microsoft 365!
Cyberattacks can happen any time, any day. No organization is immune, and the numbers are staggering, here are three attack zones and statistics for you to consider.
Embed in Your Article
This code links back to Atlantic-it.net
If these statistics have raised concerns about your cybersecurity, contact us because we can help.
Further reading


